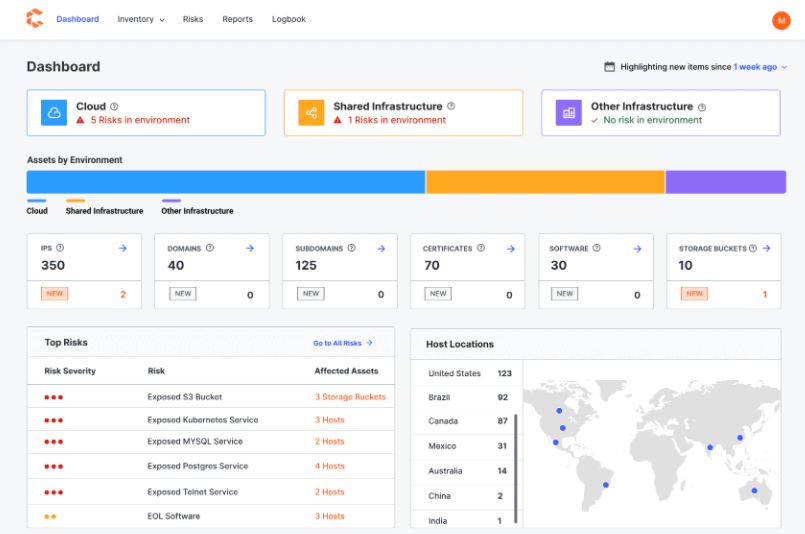
Internet attacker paths, exposed internet services, and more may all be found with Censys. Utilizing the platform, users may monitor and generate unknown assets that their workers may be used without their permission. A look from an attacker’s viewpoint may assist users to identify areas of vulnerability in their own companies. In addition to alerting users when new suspected fake certificates are discovered, the platform details assets that are impacted by vulnerabilities in real-time.
However, if Censys is not working for you anymore? due to some issues! or maybe it is down temporarily, but you don’t want to wait, then here are some of the best alternatives to Censys which you will enjoy surely.
So, don’t worry, we’ve got your back! if you want to try some other sites like Censys then here are some of the best Censys alternatives which you should try:
Best Alternatives To Censys
ZoomEye

ZoomEye is China's first internet search engine and a leading worldwide remapping service. Continuous scanning and mapping of the local or global internet are possible thanks to this software. The user will be able to more accurately pinpoint the target, reduce the likelihood of accidentally...
Alternative Details
IVRE
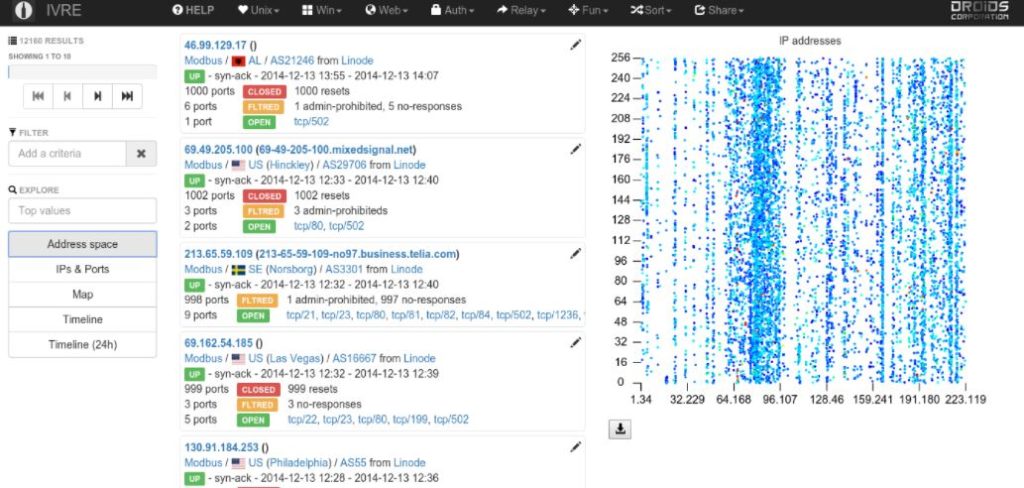
It collects network intelligence data, stores it in a database, and gives tools for analyzing it. The user-friendly interface makes it simple to navigate network flows. Zeek, Argus, and Netflow data may be imported and accessed using a CLI and Python API.
Alternative Details
Shodan

Shodan is a comprehensive search engine that lets users search and discover computers, smart TVs, routers, refrigerators, websites and literally anything. It comes with a huge range of tools that helps users to track all devices connected to the internet. It has a large number...
Alternative Details
Nexpose
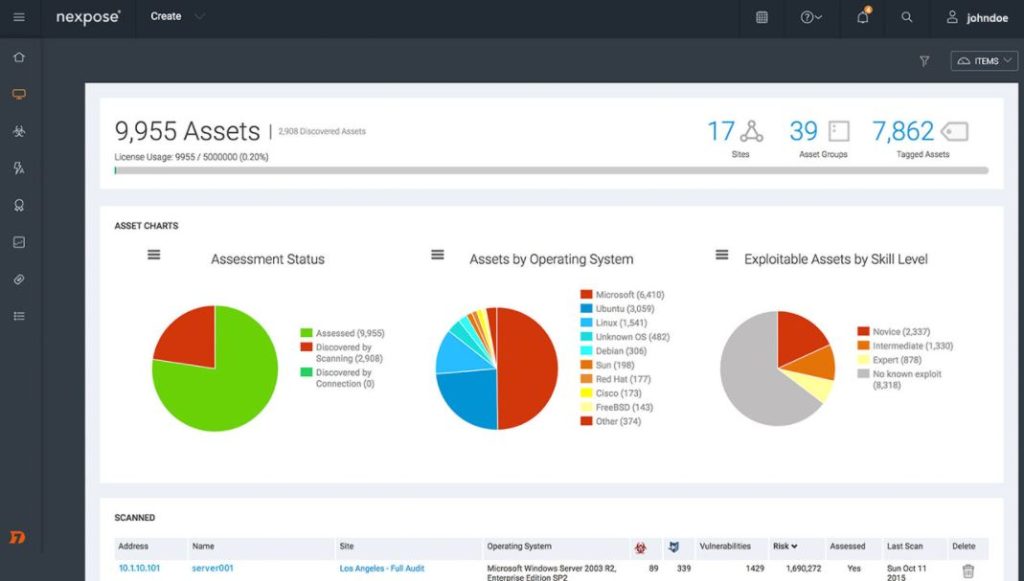
As one of the top vulnerability assessment tools, Nexpose is capable of capturing and processing large volumes of data in a timely manner while minimizing risk and providing solutions. This market-leading platform makes use of cutting-edge analytics and endpoint technologies to find vulnerabilities in real-time,...
Alternative Details
HTTPCS Security
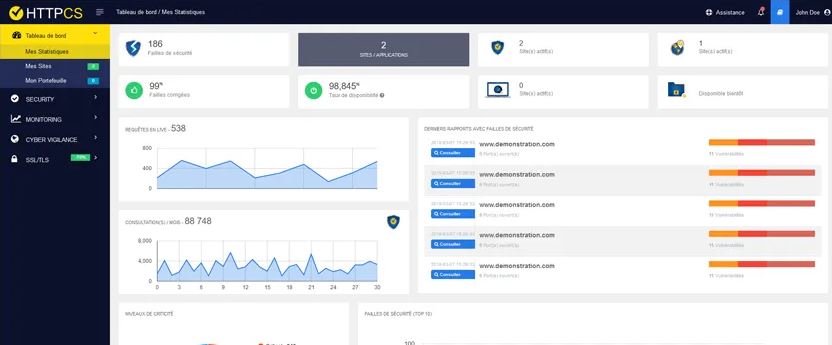
Web vulnerability scanner HTTPCS Security employs headless technology to audit 100% dynamic content of your web application or website to identify attacks. Many individuals may use it since it doesn't need any technical skills to do a vulnerability scan.
Alternative Details
OpenVAS
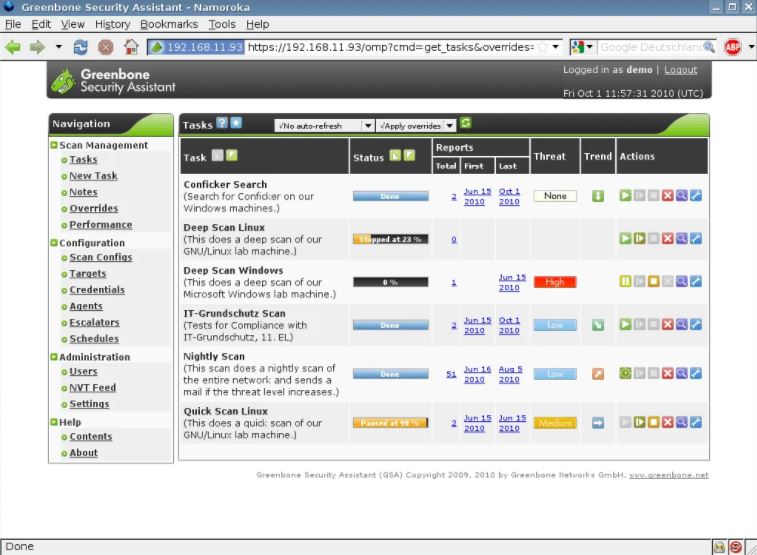
All organizations of any size may benefit from OpenVAS, a complete vulnerability assessment and management solution that includes all the essential features and capabilities. Unauthenticated testing, high- and low-level internet, industrial protocols, strong internal programming languages to execute any vulnerability test, and more are all...
Alternative Details