Metasploit simplifies network discovery and vulnerability verification for particular exploits, it improves the efficacy of vulnerability scanners with easy to use interface. Thus, actual security risk knowledge is provided, which helps prioritize repair and reduce false positives.
However, if Metasploit is not working for you anymore? due to some issues! or maybe it is down temporarily, but you don’t want to wait, then here are some of the best alternatives to Metasploit which you will enjoy surely.
So, don’t worry, we’ve got your back! if you want to try some other programs like Metasploit then here are some of the best Metasploit alternatives which you should try:
Best Alternatives To Metasploit
Cloudflare

Cloudflare helps you speed up and improve the performance of your websites, apps, SaaS services, and other comparable assets that are linked to the internet. The platform includes a collection of sophisticated technologies that allow advantages to grow in proportion to the number of servers...
Alternative Details
WebTotem
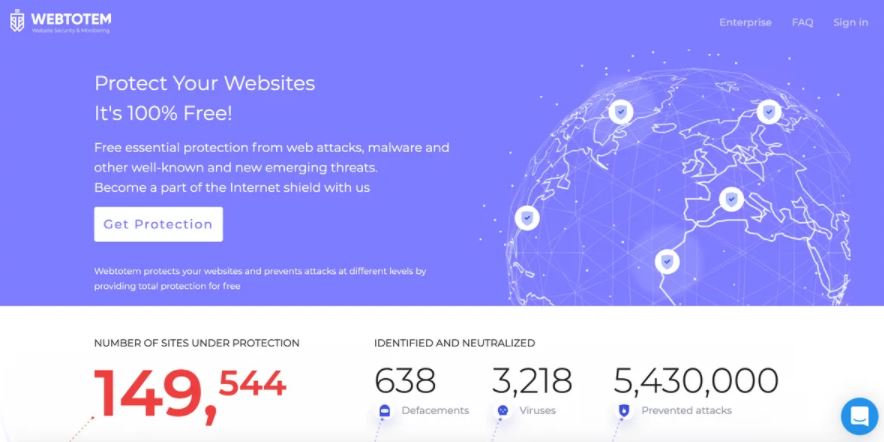
Internet service provider WebTotem offers strong solutions for safeguarding and monitoring your website in a single location that is simple to use and customizable to accommodate your needs. It helps in obtaining information about the domain and the date on which its registration is set...
Alternative Details
OpenVAS
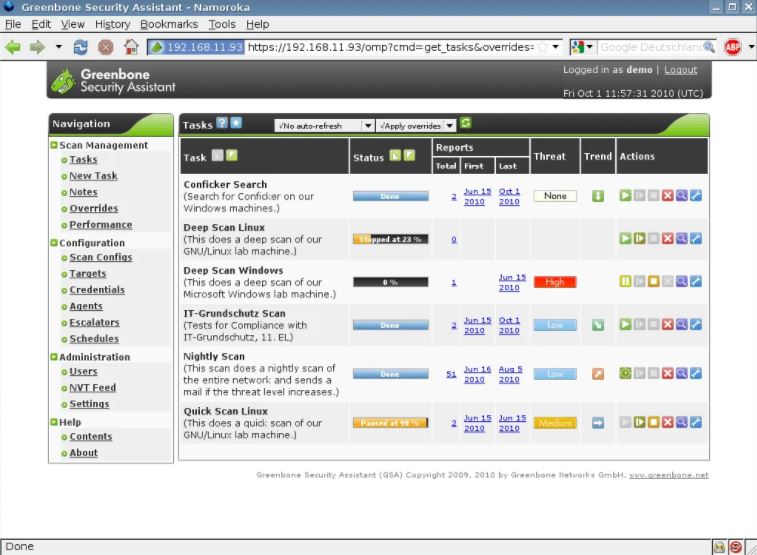
All organizations of any size may benefit from OpenVAS, a complete vulnerability assessment and management solution that includes all the essential features and capabilities. Unauthenticated testing, high- and low-level internet, industrial protocols, strong internal programming languages to execute any vulnerability test, and more are all...
Alternative Details
Nessus
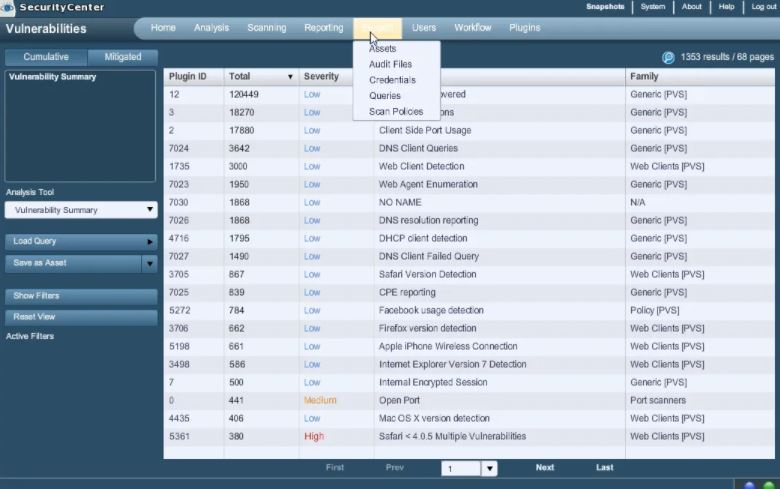
Nessus is a simple and versatile remote security scanning tool that efficiently checks a computer and notifies the user when it detects any flaws. Important features include pre-configured templates that are ready to use out of the box, customized reporting, vulnerability assessment with live findings,...
Alternative Details
Wordfence
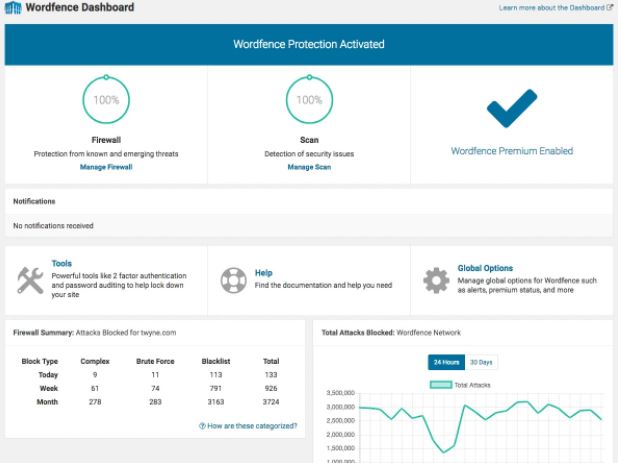
Wordfence is one of the most effective security tools. It is a complete security solution that includes all of the essential features and tools for preserving your website's integrity. Wordfence's security scanner scans the core files, themes, and installed plugins for malware, bad URLs, SEO...
Alternative Details
Acunetix
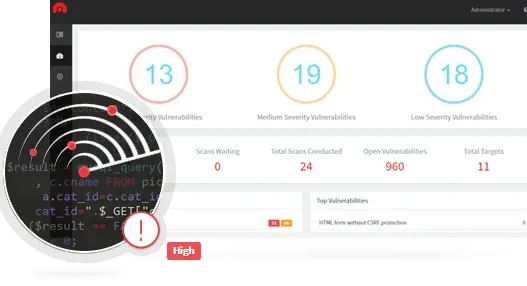
Acunetix is a feature-rich cyber-security and web-based vulnerability scanner that enables enterprises to scan and audit sophisticated, authenticated, HTML5, and JavaScript websites. Its robust vulnerability scanner aids in the accurate detection of major web application vulnerabilities, such as those found in open-source software and custom-developed...
Alternative Details
Imunify360
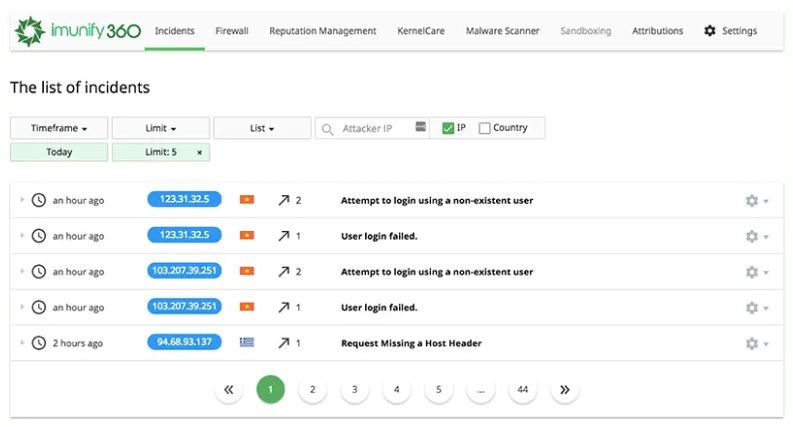
Imunify360 is a comprehensive security solution that assists customers in scanning for, identifying, and removing malware from their Linux Web Servers and other systems. It makes use of powerful technology to identify and resolve important issues such as blacklisted domains, web spam and bad bots,...
Alternative Details
Armitage
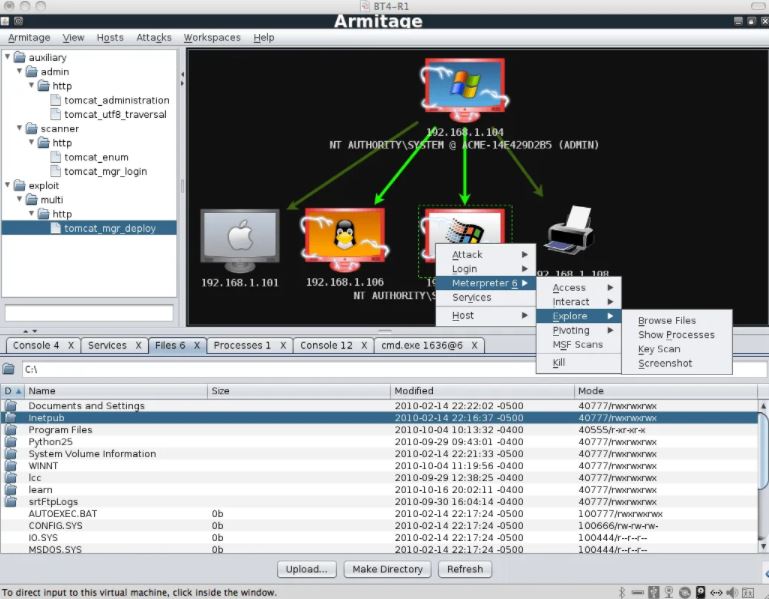
Armitage is a free and open-source cyber-attack management tool. The target database is also shown in Armitage's user interface, either in a table or a graphical manner. You may also use Armitage to launch browser exploits, build Exe files, and generate malicious files.
Alternative Details
Shodan

Shodan is a comprehensive search engine that lets users search and discover computers, smart TVs, routers, refrigerators, websites and literally anything. It comes with a huge range of tools that helps users to track all devices connected to the internet. It has a large number...
Alternative Details
HTTPCS Security
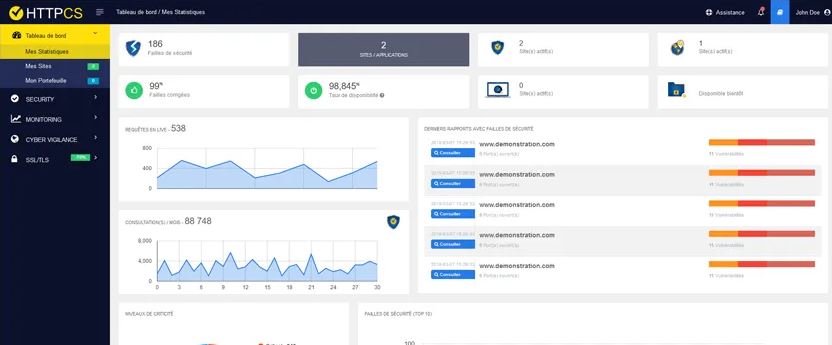
Web vulnerability scanner HTTPCS Security employs headless technology to audit 100% dynamic content of your web application or website to identify attacks. Many individuals may use it since it doesn't need any technical skills to do a vulnerability scan.
Alternative Details
ZoomEye

ZoomEye is China's first internet search engine and a leading worldwide remapping service. Continuous scanning and mapping of the local or global internet are possible thanks to this software. The user will be able to more accurately pinpoint the target, reduce the likelihood of accidentally...
Alternative Details
Sucuri

Sucuri is an online web security platform that offers advanced cloud-based technology and service for any kind of web security. It is a free easy-to-use application that does not require any installation or signup. The best thing about Sucuri is that it works on all...
Alternative Details
Intruder
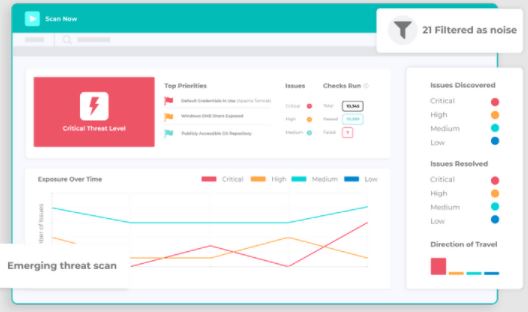
Intruder is the most sophisticated cloud-based vulnerability management solution built for small and medium-sized enterprises. It assists with threat monitoring, configuration mapping, risk assessment, bug detection, and other security-related tasks such as network monitoring and analysis. It examines the information of ports, identifies deployments, and...
Alternative Details
WebARX
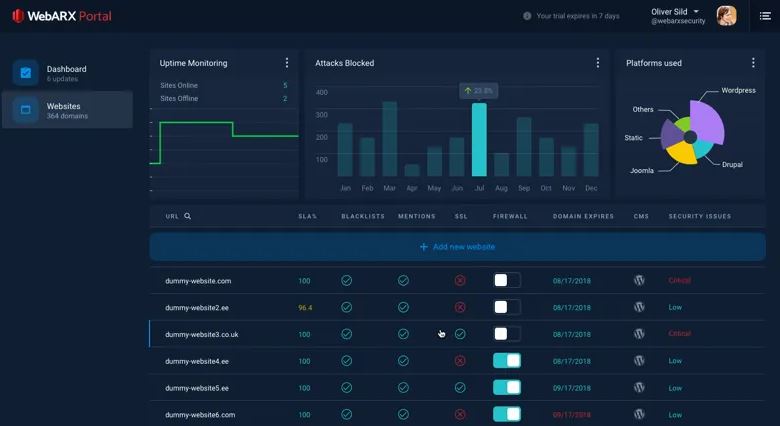
WebARX is a web-based solution that assists customers in protecting their websites against plugin vulnerabilities. It provides a dashboard that allows users to keep track of any potential security vulnerabilities on all of their websites from a single location. Users may produce security reports on...
Alternative Details
w3af
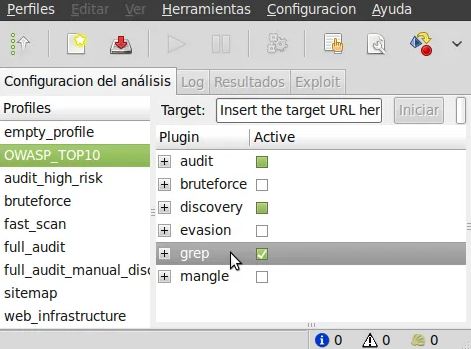
w3af is a Web Application Attack and Audit Framework. The framework is proudly designed in Python to be simple to use and modify, and it is open source. Its purpose is to provide a framework that will assist you in securing your web apps by...
Alternative Details